Solving LetsDefend SOC140 - Phishing Mail
Let’s dive into solving the LetsDefend SOC140 challenge, where we’ll be analyzing a phishing email with a PDF attachment.
Sebastian Salazar
12/6/20245 min read
Hi! This is my take on solving LetsDefend SOC140 - Phishing Mail.
Let’s start by reviewing the summary that LetsDefend provides to us. We can also begin creating the case and running the playbook to guide us through the investigation!
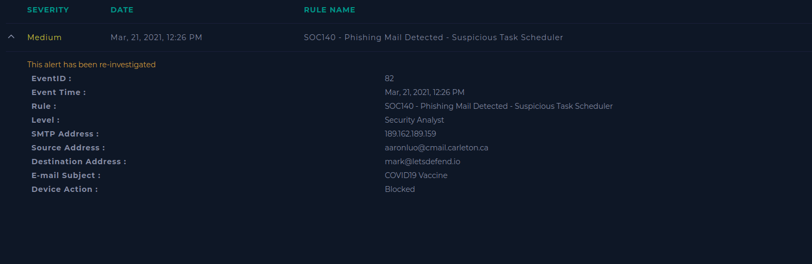

Short tip: We can gather a lot of information here, and we’ll be moving between many webpages. So, I like to start by writing everything down in a notepad. This way, I won’t lose any information and won’t have to keep going back and forth to this summary. Like this:
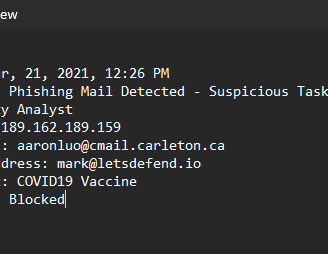
Ok lets start with the Playbook! first page:
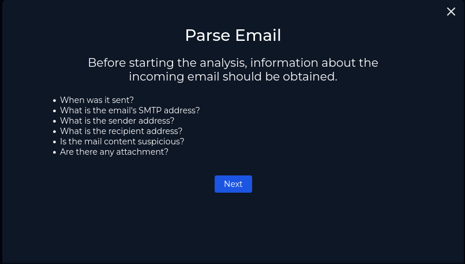
Let’s parse the email, as there are some pretty important questions to answer!
My approach again is to copy all the questions and write them down in my notepad, which will also have all the answers, by the way.
So, here’s how my investigation is looking at the moment.
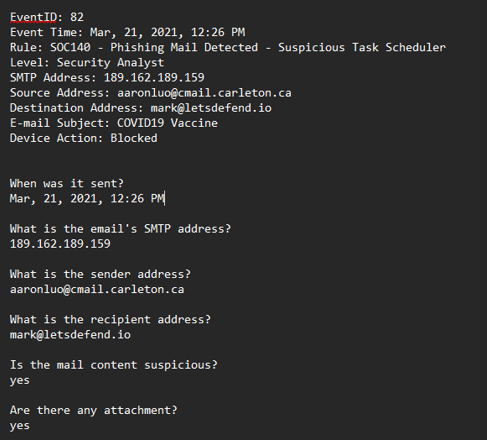
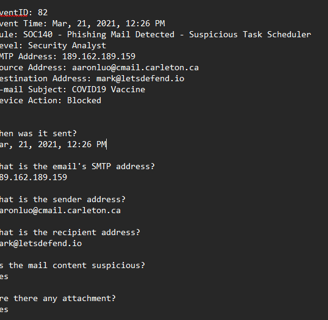
As you can see, the answers to every question are actually right there.
The date, SMTP address, sender, and receiver addresses are all visible.
For the last two questions, we need to look at the actual email in the Practice Tab on Email Security. We can filter by the sender address, and it’s the one related to the COVID VACCINE, as we can see in the email subject.
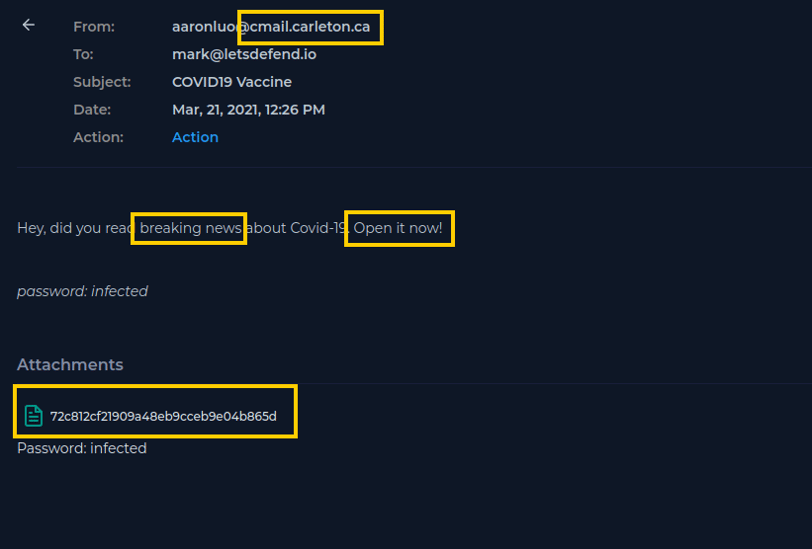
Let’s take a look at the actual email...
Does the email look suspicious?
Well, it’s a pretty simple email, but the first thing we notice is the actual email domain: @cmail.carleton.ca. I Googled it and found out that it’s a university email. A little weird that Aaron from Carleton University is sending us COVID vaccine information.
Next, we can see it has a sense of urgency. Phrases like “Breaking News” and “Open it now” make us feel like we need to open it immediately! Haha.
And the attachment—yep, it has an attachment, which makes it even more suspicious. With this analysis, we can answer all the questions related to the first step of the playbook! Yay, next page!
The email contains an Attachement, so we click on yes!
Here comes the fun part! Attachement Analysis.
The first thing I did was analyze the actual link to download the file. I put it on VirusTotal, and there it is—it's malicious! Case solved!
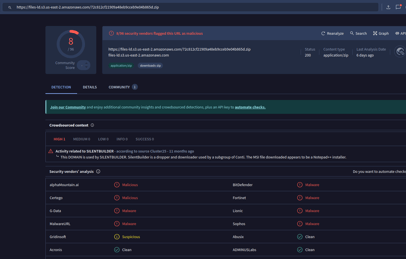
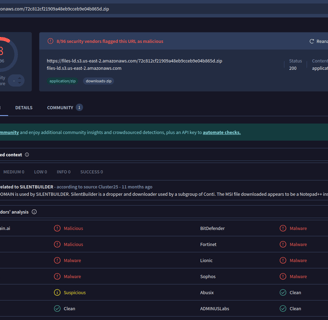
Nah, let’s deep dive into it and make sure we can securely say that this file is malicious!
We can actually download the file and examine what’s inside, so that’s exactly what I did. I unzipped the file, and inside, we find a PDF file.
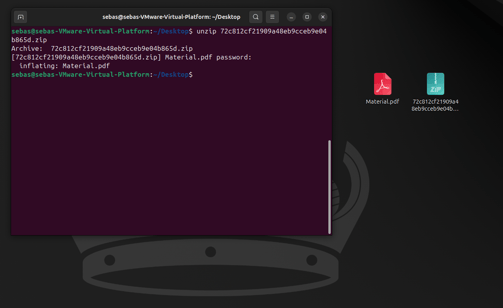
PDFs can contain malicious URLs and attachments that can be dangerous. They’re a great way to hide malware inside a trusted file format that everyone uses!
Let’s see what’s inside. I don’t want to open the file directly, so we’ll use tools to analyze the contents without actually opening the PDF.
Didier Stevens has a great set of tools for phishing analysis, and in his suite, there are a couple specifically for PDF analysis. We’ll be using them.
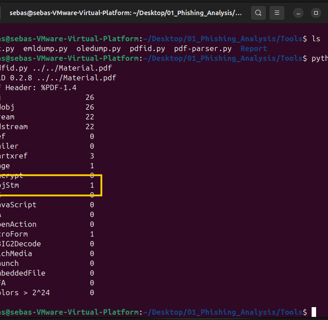
First, let’s take a look at the content of the PDF using pdfid.py. We can see that there are no attachments and no URI in the PDF—maybe it’s legit? But then I noticed an object named ObjStm, and I wasn’t sure what it was, so I Googled it.
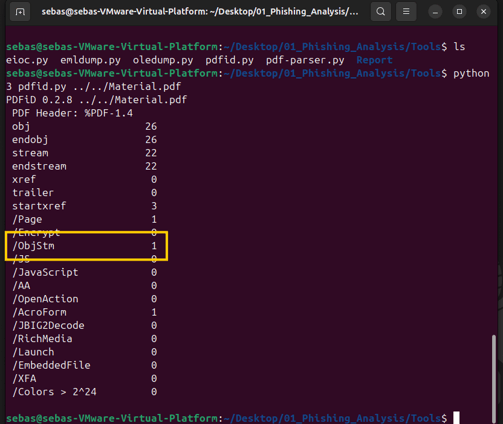
And here’s Didier Stevens saving us once again! On his blog, he made a post titled:
Analyzing a Phishing PDF with /ObjStm
In the post, he explains that sometimes attackers hide URIs inside a stream object called /ObjStm. If you want to learn more, you can check out his blog—it's pretty cool! He also explains how to use his tools to investigate this kind of PDF object. For this investigation, we’ll be using pdf-parser.py.
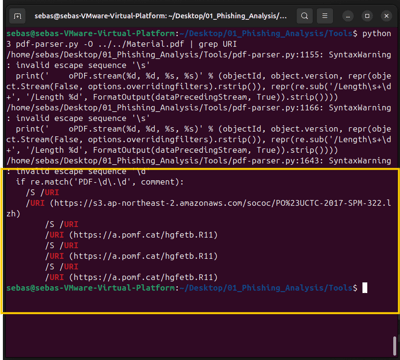
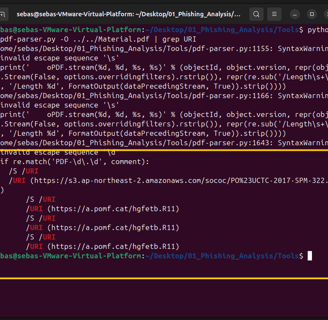
I just used grep to search for "URI" and check if anything was hidden there.
And there it was—this weird-looking URI, tucked away inside the PDF.
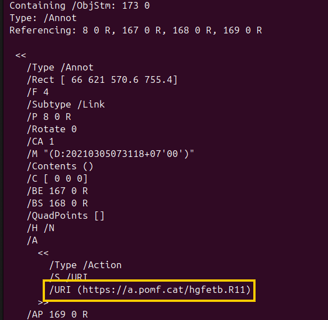
I decided to double-check if it was actually the /ObjStm object. So, I removed the grep command and looked for the object details, and there it is:
The /ObjStm object was hiding this URL!
Let’s check this one on VirusTotal.

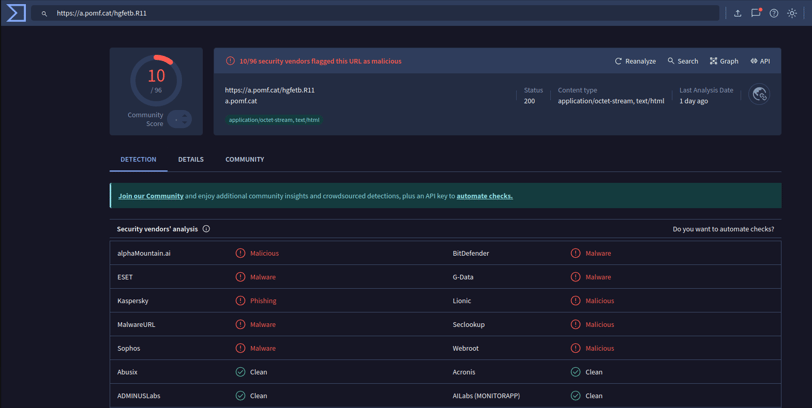
And what about Hybrid Analysis:
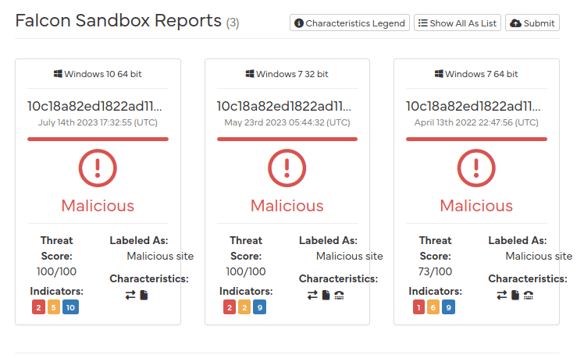
Alright, I think we have our conclusions. We could run it in a sandbox to analyze its behavior, but that’s a task for another time, haha.
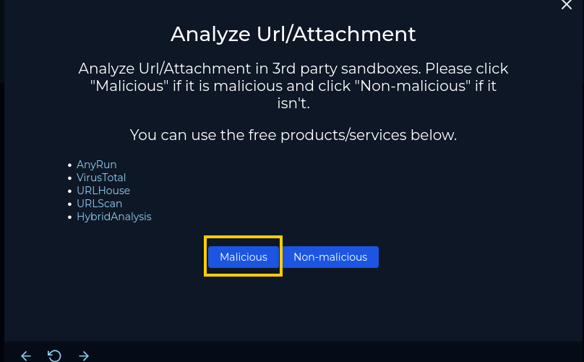
The email attachment is malicious! On to the next step!
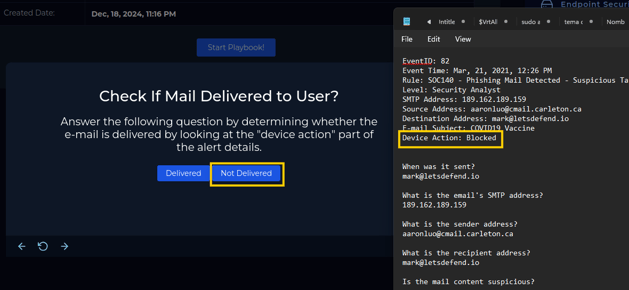
Now let’s check if the email was delivered. In the notes we’ve taken, we have the "Device Action" field, and we can see that the device blocked the download. So, we can confirm it was marked as "Not Delivered."
In the notes we’ve been taking, we included the action that occurred on the device. We can see that it was blocked, so thankfully, it wasn’t delivered! :)
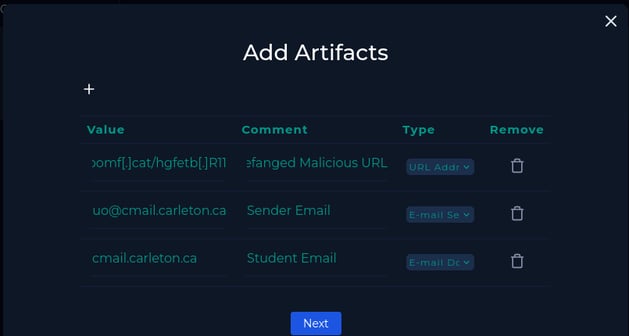
Here, we can add all the artifacts collected during our investigation, such as the malicious URL (which I defanged using CyberChef), the sender's email address, the student domain, etc.
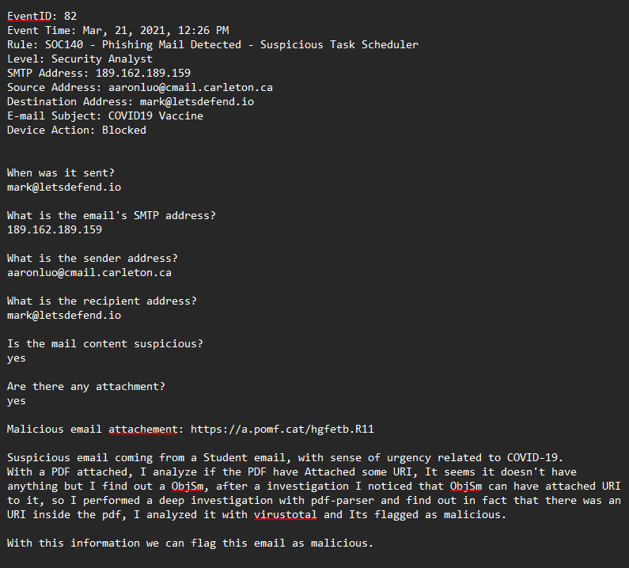
And the last part is related to writing all the investigation notes—here are mine!
I’m not sure if they’re the best notes, especially considering that I wrote ObjStm wrong, haha.
I copied and pasted them into the field and selected "Next." Now it’s time to send our final answer! Was this email a False Positive or a True Positive?
Thanks for reading this walkthrough! I hope it was helpful for everyone. I’m still learning, so apologies if I made any mistakes during my investigation process.
Also, shout-out to Let’s Defend for creating these challenges to help us gain more experience in cybersecurity! Here’s the link to the platform: